Ledger Reveals Critical Wallet Password Flaw
Ledger provides a brute-force vulnerability of Tangem crypto cards. Weak passwords are subject to easy hacking without a patch fix. It is time to enhance security among users.
Ledger has discovered a disastrous flaw in cryptocurrency wallets with Tangem cards. The bug uses a tearing attack to overcome security delays to brute force logins at a higher rate. The realization evokes serious issues regarding wallet security.
Ledger Donjon team has unveiled this problem following an elaborate examination of the secure channel and password protection of Tangem.
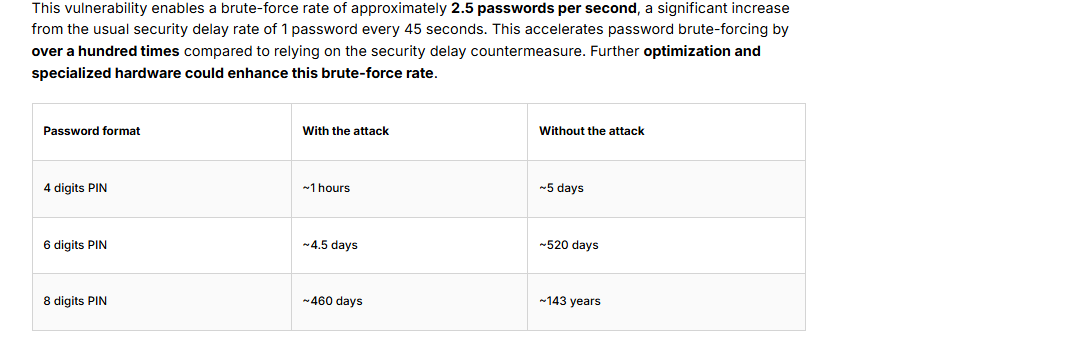
Although Tangem has a built-in delay counter in order to make the retrieval of passwords more difficult, now the attackers can make about 2.5 passwords per second. This is more than 100 times faster than the planned rate of one guess in 45 seconds.
The way the Attack Destroys Wallet Security.
Tangem cards have a security system that postpones password re-entering in case of failure. A lost attempt will create a delay of up to 45 seconds.
This tends to render brute-force attacks unfeasible, particularly on longer passwords. The attack takes advantage of a tearing method that cuts off the power supply of the card at critical functions.
This makes the failure counter of the card fail to update in the proper way. Consequently, the attackers are able to bypass the delay and attempt passwords nearly indefinitely.
Research in which Ledger called the timing window of a card to power off in a narrow time range of about 6700 microseconds prevented the security delay from occurring.
With power disconnection in addition to analyzing electromagnetic emission of the chip in the card, attackers can also determine whether a password guess is correct before they delay by the signal.
The security channel encryption provided by Tangem, which is developed to secure the exchange of data, adds to the weakness.
The value of the key used in encryption is based on the user’s password. This makes cracking the encryption of the channel just as hard as cracking the password.
Ledger experimented with equipment priced below 5000 dollars thus as a result, the attack could be made available to numerous attackers with physical access.
Regrettably, there is no patch to correct this defect on the current version of Tangem cards.
Serious Risks for Weak Password Users
Source ledger.com
Common or weak passwords are highly susceptible to such an attack. To illustrate, a 4-digit PIN is hackable in just under an hour, as compared to five days without the intrusion.
Six or eight-character passwords are also significantly weaker, which is still more secure.
Tangem recommends that its users use passwords that are at least eight characters in length, containing letters, numbers, and symbols.
It is important because simple or dictionary-based passwords can be broken in days rather than years.
In his report, which was duly disclosed to Tangem, Ledger advised the implementation of a password policy by using strong user passwords, which they advised entitled the users to do. Weak password users need to upgrade to minimize risk. Tangem has understated the risk by saying that the problem is not vulnerable. The technical analysis that Ledger provides, however, highlights the fact that there are real-life breaches, which can be damaging.
You May Also Like

$1.77 Trillion Asset Manager T. Rowe Price Submits Crypto ETF Application

Crypto News: Cardano Founder Steps In as Kadena Faces Major Token Collapse
